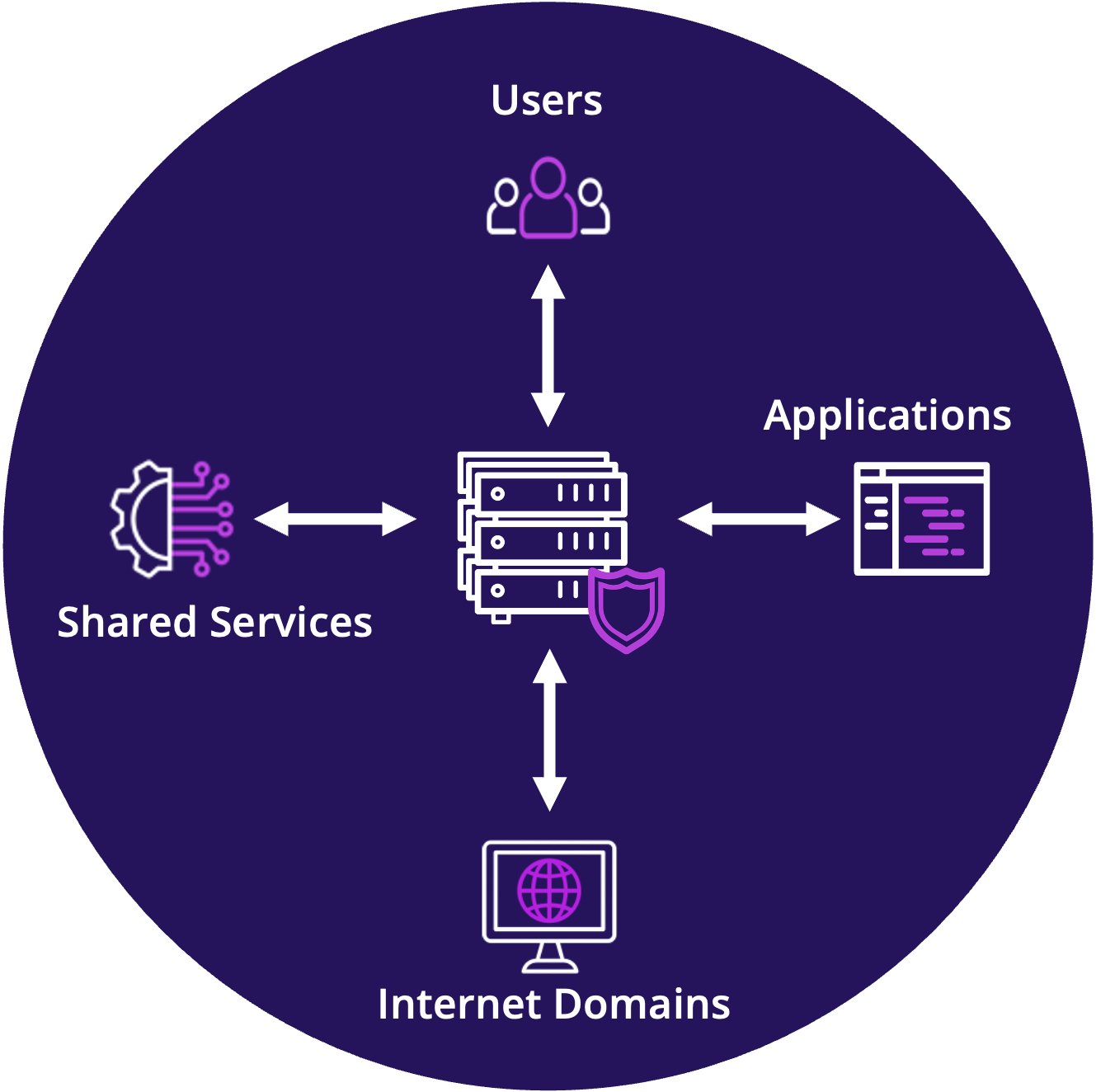
360° Workload Protection
Continuous Zero Trust-based Protection from Code to Cloud
Secure workloads against supply chain, ransomware, and runtime attacks in production.
Prismo's Zero Trust based Security Platform provides automated vulnerability management, full lifecycle protection against known and zero day threats, and real-time protection in production.
Threats actors are increasingly targeting workloads
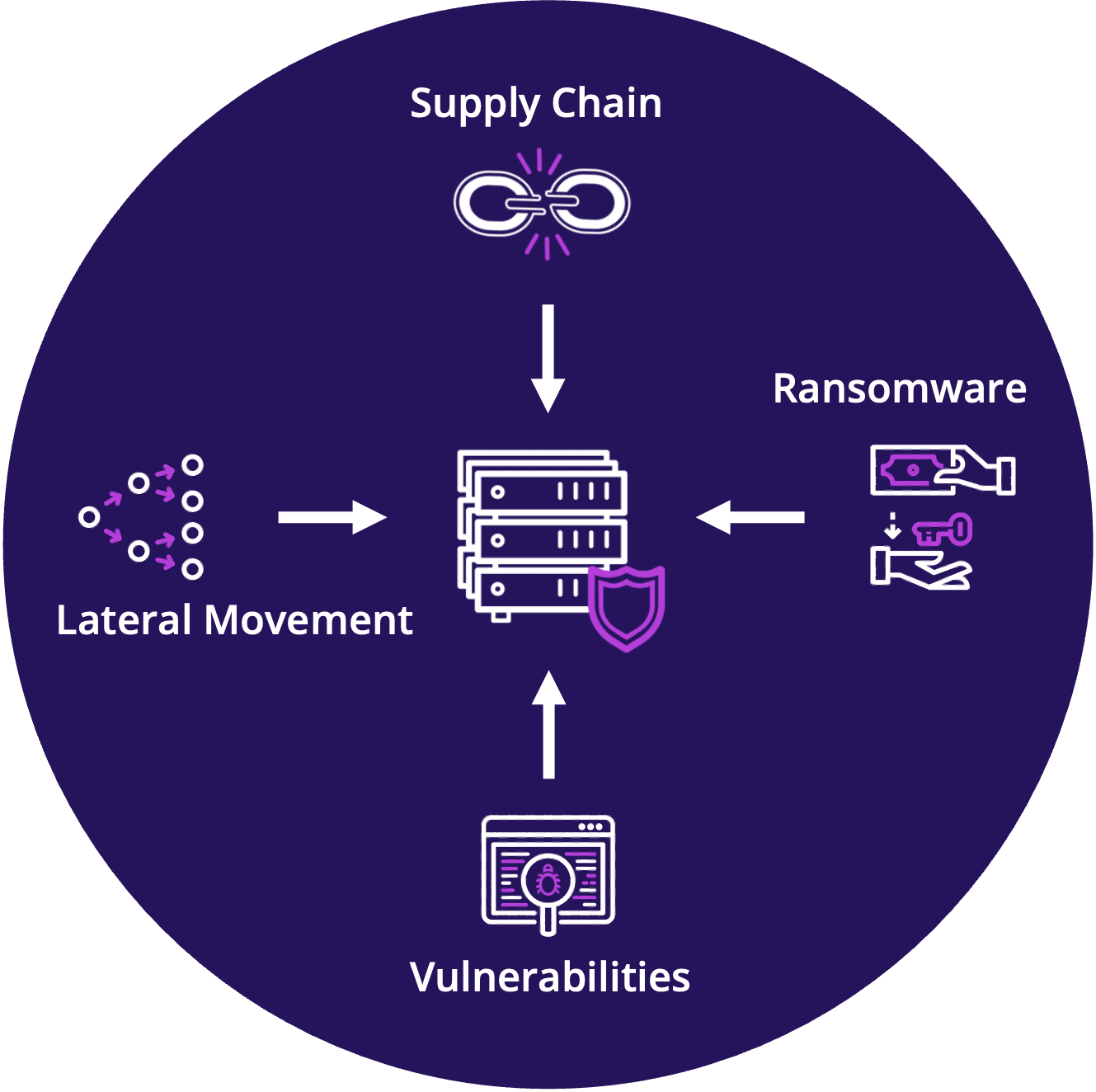
Today, the infrastructure that runs your code and software is continuously targeted by threat actors via:
- Exploitation of known and zero-day vulnerabilities
- Lateral movement across the network and enterprise
- Installation and detonation of ransomware
- Sophisticated supply chain attacks
Attacks against workloads bypass conventional security controls
Today's advanced threats can't be prevented with endpoint protection or network micro-segmentation alone.
Detect & Contain a Breach
Open Source Attacks
Growth in Attacks
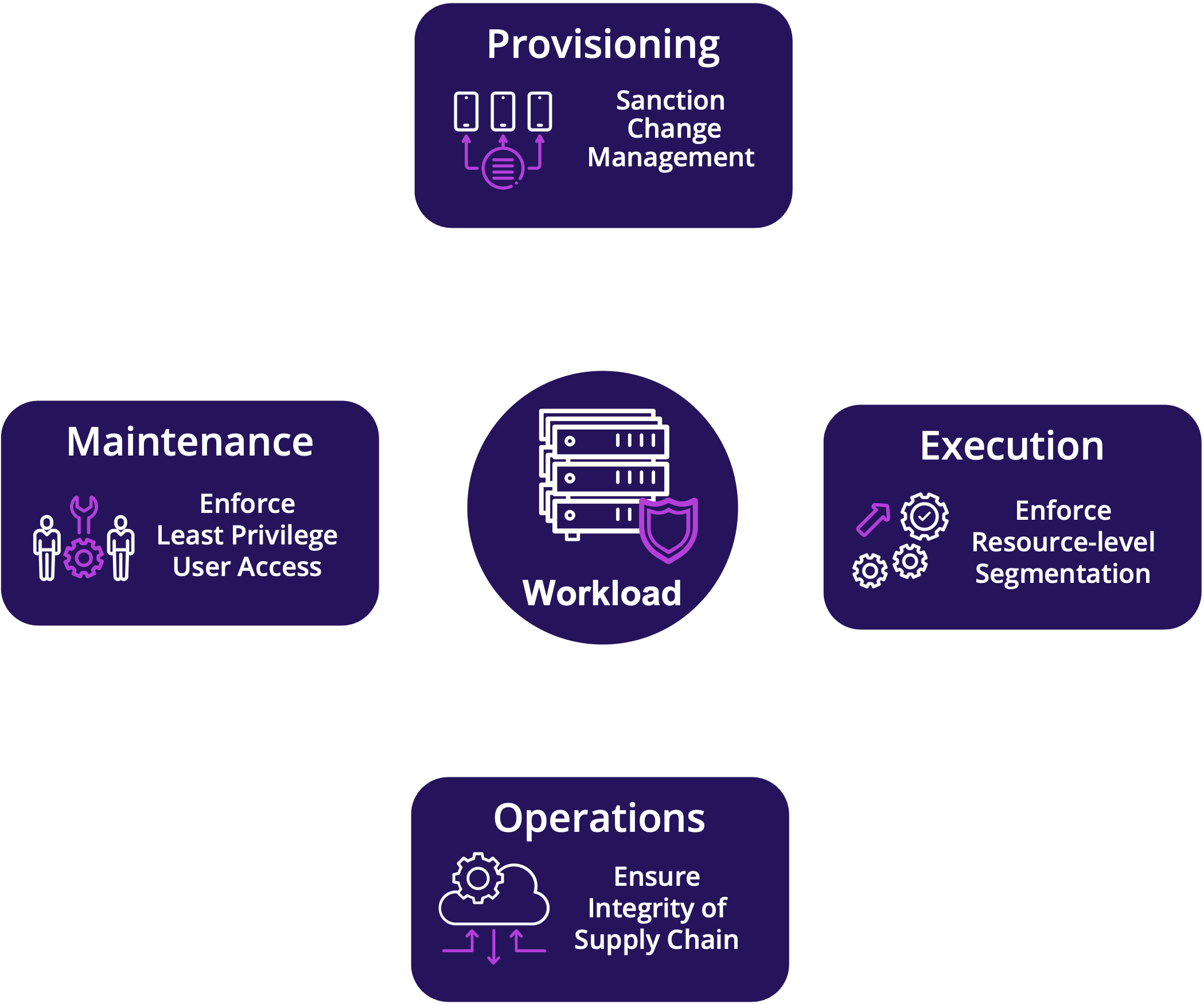
Prismo provides full-lifecycle protection for workloads
Proactively protect workloads across provisioning, operations, execution, and maintenance functions.
Prismo protects the physical and virtual workloads that run your code across their entire lifecycle and ensures high security for highly fluid environments.
- Provisioning: Starting from a verified golden image with a CIS hardened configuration, Prismo validates integrity of all subsequent installs, library updates, vulnerability patches and configuration changes.
- Execution: System and network application behavior is profiled to granularly authorize access to every resource. Segmentation is automated with what-if, dry-run, and intent-based policies to eliminate human error.
- Operations: Tasks performed by scripts, service accounts, and tools are discovered and fingerprinted to detect and block backdoors in sanctioned channels.
- Maintenance: Standing access to production servers is denied by default. Just-in-Time (JIT) certificate-based pin-holes are dynamically provisioned to allow support personnel to perform only authorized tasks.
Ensure the integrity of your
supply chain software
Fingerprint commercial and open source software and whitelist behavior
to protect against backdoors and zero-day exploits
Open-Source and commercial software are susceptible to backdoors and vulnerabilities making the enterprise vulnerable to supply chain and ransomware attacks. Prismo ensures the integrity of the software supply chain by:
- Automatically building an execution profile of images that includes 3rd party applications, open source and OS
- Extracting the security fingerprint and certifying the image against industry standard frameworks ( CIS, MITRE, and NIST)
- Programmatically verifying the certified fingerprint is consistent between upgrades, patches, and in production
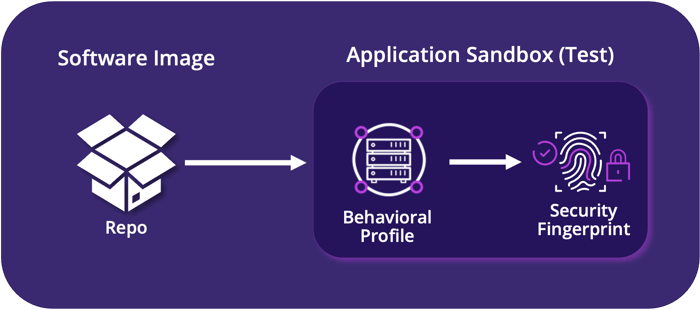
Prismo Supply Chain Software Workflow
Protect workloads from ransomware
Proactively protect workloads against ransomware to avoid operational disruption and business impact
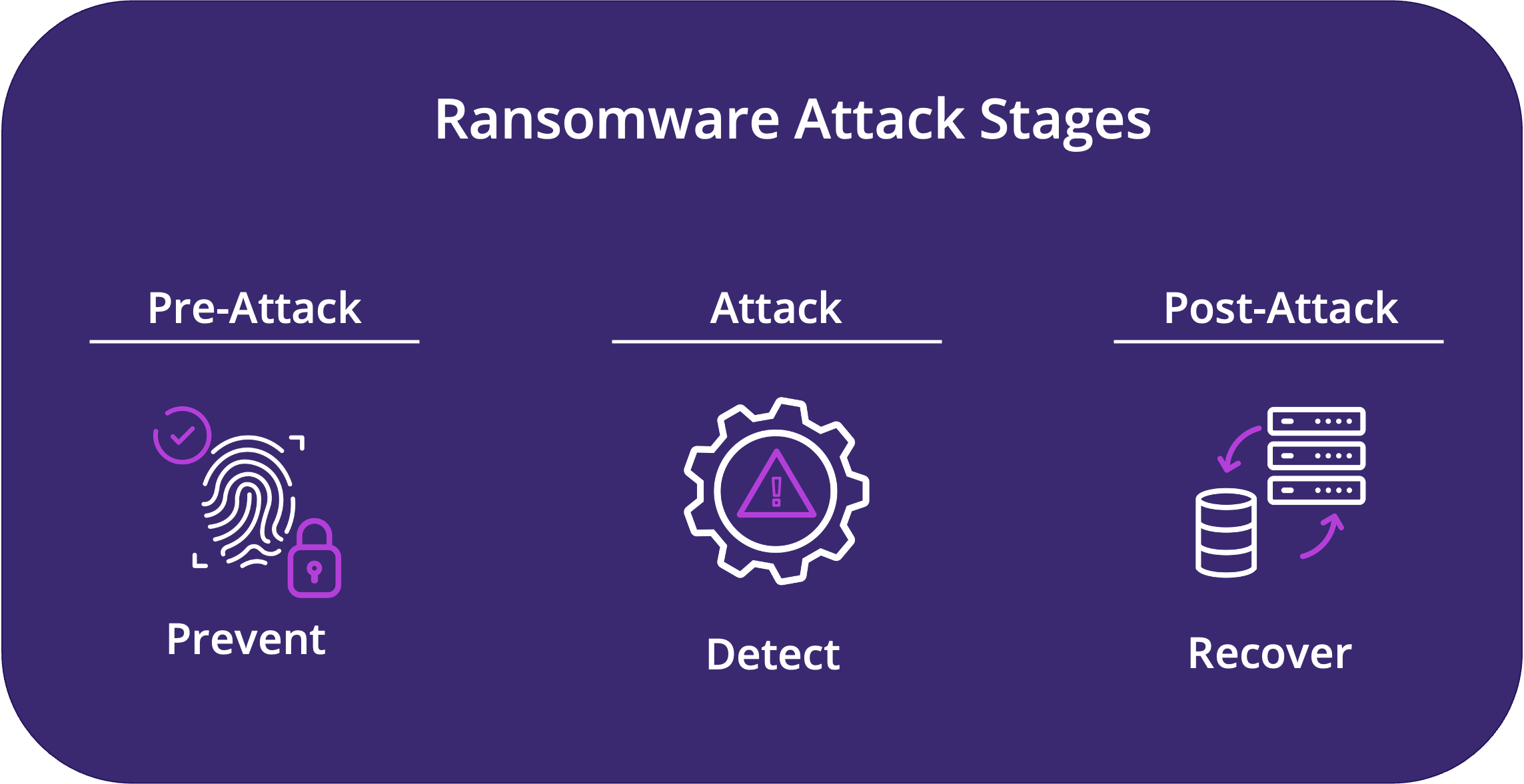
Myriad attack vectors such as phishing emails, infected websites, malvertising, fake applications, and infected storage devices make it virtually impossible for organizations to keep ransomware out of their environments entirely. Prismo provides proactive protection, early detection, and real-time response to mitigate ransomware at all stages of an attack:
- Pre-Attack: Ransomware is proactively blocked at install time by restricting the provisioning of software to sanctioned channels.
- Attack: In the event of a compromise, Prismo rapidly detects ransomware-specific behaviors and blocks lateral movement to minimize dwell time.
- Post Attack: Prismo increases cyber-resiliency by providing "server-rollback" capabilities to quickly restore affected systems, minimizing operational disruption and business impact.
Protect workloads with
resource-level segmentation
Fine-grain segmentation of all workload-related resources secures physical and virtual workloads
Work from Anywhere
with Secure Virtual Desktops
Isolate the enterprise from risky end-user behavior and activities
The Benefits of Zero Trust-based
Workload Protection
Prismo reduces risk, increases agility and responsiveness, and cuts costs
Minimizes the security exposure surface even for fully distributed architectures and operations
Enables organizations to pursue new business opportunities and respond more quickly to market changes
Zero Trust architecture leverages real-time automation to slash direct and indirect security costs
Customers Agree
Secure internal applications against external and internal threats
"Prior to implementing Prismo, we carried significant security risk due poor visibility, control, and lack of accurate insights. We didn't have the ability to control user access to resources, and tasks were manual, taking up to 4 to 5 hours to complete. With Prismo, I don’t have to ask my staff to pull and piece together data and reports. Now, information is at my fingertips, I can create reports with 1-click, and the management team has greater confidence we are secure."